BOAT: Buffer Overflow Attacks on IoT devices
-
START DATE
1 Oct, 2018
-
END DATE
30 Sep, 2021
DETAILS
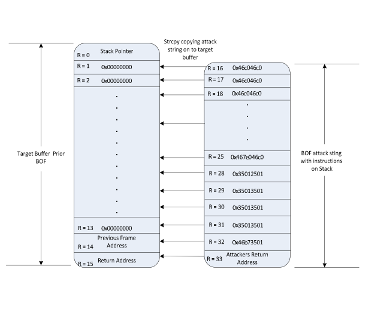
The vulnerability of electronic systems to attacks from hostile agents over the Internet is a matter of growing concern as the digital world becomes increasingly interconnected. Many countermeasures have been put in place to address these concerns, but the computational burden they impose may be excessive for low-power devices. In particular, the devices which comprise The Internet of Things are particularly vulnerable.
This project involves the analysis of such Buffer Overflow (BOF) attacks. We explore an extensive range of attacks including return-to-lib-c and code injection on a representative IoT operating system (namely FreeRTOS) and on a range of Linux distributions running on an ARM-based single board computer typical of “high-end” IoT devices. Our testbed allows us to identify trends and commonalities in BOF vulnerabilities among numerous operating systems widely deployed in IoT systems and to generate numerical assessments of their vulnerability to this class of attacks. Our research will help in identifying OS vulnerabilities and how to mitigate them, so as to prevent the compromise of IoT systems for data infiltration or exfiltration, or their co-option into “botnets”.
Student(s): Gary Mullen, Blas Molina Calatayud
Publications
- G. Mullen and L. Meany, “Assessment of buffer overflow based attacks on an IoT operating system”, 2019 global IoT summit (GIoTS), 2019
- B. Calatayud and L. Meany, “A comparative analysis of buffer overflow vulnerabilities in high-end IoT devices”, 2022 IEEE 12th annual computing and communication workshop and conference (CCWC), 2022.

